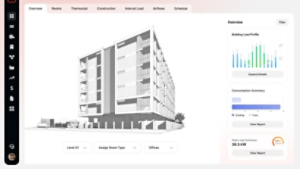
- Services
- Products & Systems
- Training & Support
- Industries
- About
-
-
-
Latin America
- Argentina Spanish
- Mexico Spanish
- Brazil Portuguese
- Aruba English
- Bahamas English
- Belize English
- Bermuda English
- Bolivia Spanish
- Bonaire English
- Chile Spanish
- Colombia Spanish
- Costa Rica Spanish
- Dominican Republic Spanish
- Ecuador Spanish
- El Salvador Spanish
- Grenada English
- Guadeloupe English
- Guatemala Spanish
- Guyana English
- Haiti English
- Jamaica English
- Martinique English
- Netherland Antilles English
- Nicaragua Spanish
- Panama Spanish
- Paraguay Spanish
- Peru Spanish
- Puerto Rico Spanish
- Saint Lucia English
- St. Vincent & Grenadines English
- Suriname English
- Trinidad & Tobago English
- Venezuela Spanish
-
-
Europe
- Armenia English
- Austria German
- Azerbaijan English
- Belgium French Dutch English
- Croatia Croatian
- Czech Republic Czech
- Denmark English
- Estonia English
- Finland English
- France French
- Georgia English
- Germany German
- Greece Greek
- Hungary Hungarian
- Israel English Hebrew
- Ireland English
- Italy Italian
- Kazakhstan English
- Kyrgyzstan Russian
- Latvia English
- Lithuania English
- Luxembourg French German
- The Netherlands Dutch
- Norway English
- Poland Polish
- Portugal Portuguese
- Romania Romanian
- Serbia English
- Slovakia Czech
- Slovenia English
- Spain Spanish
- Sweden Swedish
- Switzerland French German Italian
- Turkey Turkish
- Ukraine English
- United Kingdom English
- Tajikistan Russian
- Turkmenistan Russian
- Uzbekistan Russian
-
-
Asia Pacific
- China Simplified Chinese English
- Korea, Republic of (South Korea) Korean English
- Vietnam Vietnamese English
- India English
- Australia English
- Japan Japanese
- Guam English
- Thailand Thai English
- Taiwan Traditional Chinese English
- Hong Kong SAR English
- Indonesia English
- Malaysia English
- Philippines English
- Singapore English
- New Zealand English
ComfortSite Login
Trane ComfortSite is an extranet site designed to save you time. With your secure login, you can:
- Order Equipment, Parts, Literature and track Order Status
- View product literature
- Register for Training programs
- Complete Warranty requirements online
- Search for specific Product Information
- Use interactive Product Support functions
- View and print invoices through Account Track Online
- and More
Trane Connect
This is the login for Trane® Connect™ and other Trane® commercial applications. Trane® Connect™ is our secure, cloud-based customer portal to access your building systems to remotely monitor and manage building systems, and conduct routine maintenance.
Select Your Language
Selecting a language changes the language and content on the Trane site.
- Argentina Spanish
- Mexico Spanish
- Brazil Portuguese
- Aruba English
- Bahamas English
- Belize English
- Bermuda English
- Bolivia Spanish
- Bonaire English
- Chile Spanish
- Colombia Spanish
- Costa Rica Spanish
- Dominican Republic Spanish
- Ecuador Spanish
- El Salvador Spanish
- Grenada English
- Guadeloupe English
- Guatemala Spanish
- Guyana English
- Haiti English
- Jamaica English
- Martinique English
- Netherland Antilles English
- Nicaragua Spanish
- Panama Spanish
- Paraguay Spanish
- Peru Spanish
- Puerto Rico Spanish
- Saint Lucia English
- St. Vincent & Grenadines English
- Suriname English
- Trinidad & Tobago English
- Venezuela Spanish
- Armenia English
- Austria German
- Azerbaijan English
- Belgium French Dutch English
- Croatia Croatian
- Czech Republic Czech
- Denmark English
- Estonia English
- Finland English
- France French
- Georgia English
- Germany German
- Greece Greek
- Hungary Hungarian
- Israel English Hebrew
- Ireland English
- Italy Italian
- Kazakhstan English
- Kyrgyzstan Russian
- Latvia English
- Lithuania English
- Luxembourg French German
- The Netherlands Dutch
- Norway English
- Poland Polish
- Portugal Portuguese
- Romania Romanian
- Serbia English
- Slovakia Czech
- Slovenia English
- Spain Spanish
- Sweden Swedish
- Switzerland French German Italian
- Turkey Turkish
- Ukraine English
- United Kingdom English
- Tajikistan Russian
- Turkmenistan Russian
- Uzbekistan Russian
- China Simplified Chinese English
- Korea, Republic of (South Korea) Korean English
- Vietnam Vietnamese English
- India English
- Australia English
- Japan Japanese
- Guam English
- Thailand Thai English
- Taiwan Traditional Chinese English
- Hong Kong SAR English
- Indonesia English
- Malaysia English
- Philippines English
- Singapore English
- New Zealand English